Hacking, Phishing, Spoofing, Pharming, Scamming, Malware, Scareware, Ransomware, Spyware, Virus, Worm. So many terms. So many concerns. Caregivers have enough to worry about without having to worry about recovering from a computer hack. Therefore, it’s increasingly important to educate the people we care for about the digital invaders trying to hack their personal information and money. The better we understand the tactics, the better we can protect ourselves and our loved ones from the scams.
[Keep in mind as you read this article, you don’t need to click on any links. Just enter the URL address in a new tab. Getting into this habit will make you safer in the long run.]
It all starts with Hacking:
Think of hacking as breaking and entering for the digital (computer) age. A hacker finds a way into a system (your computer) to gain access to information. You’ve likely heard this term a lot with media reporting on email hacks. Being hacked means that someone has found a way to gain access to your computer and as a result, to gain access to your personal information kept on that computer. The most common way in is through emails. But be aware, hackers don’t just get your information from your personal computer. They also hack into company computers that store your information.
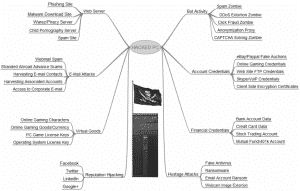
This diagram, from the windows club (check out the entire article at http://www.thewindowsclub.com/why-someone-want-hack-computer) is a thorough demonstration of what hackers are seeking. (Sorry for the blurry image. Go to the original article to see the details. This just gives you an idea of how many ways hackers use information.)
Once someone is in your computer they use it to get to everything else. Here’s another great article on the ways hackers use email information: https://heimdalsecurity.com/blog/hacked-email-why-cyber-criminals-want-inbox/
The key to protecting your information is to avoid being hacked in the first place (though 100% protection is out of your hands, because your information is in someone else’s hands). So let’s start with the most common, most vulnerable approach to hacking…
Email Phishing:
Yes, phishing as in fishing. The hacker throws out bait to get you to click on a link. Sometimes that link will take you to a “website” which will ask for personal information, including passwords. Sometimes that link downloads a virus or malware to your computer giving the hacker access to your computer, and thus your personal information. So any time you come across a link or attachment in an email, BE SKEPTICAL, THINK TWICE, and TAKE A CLOSER LOOK. Here’s how to approach emails that want you to click a link:
- QUESTION, QUESTION, QUESTION. Any time there is a link or attachment, do not click on either until you confirm it’s safe.
- If the email contains ONLY a link or attachment, don’t click on it.
- Eve if the email is from a friend, you need to check twice. If the email only contains a link or attachment, ask your friend directly if they sent it, and if they know the source of the link or attachment. (They may have unsuspectingly sent you a hack because they thought it was okay.) If you routinely only copy and paste URL’s this will provide some protection.
- Question emails that come from companies. Just because there’s a company logo doesn’t mean it is really from that company.
- Check the email address. Does the email extension (@…) include the company’s URL? (URL is the website address). Here’s an example of a deceitful email. It’s not really from Discover, even though the content looks very real. Note the “from” email address. It’s not from Discover.
- Even if the URL has the company name in it, it may not be legitimate? As in this Paypal URL. Notice that “paypal” is in URL but it has a string connected to it: paypal . notification . yaraneaftab . ir. It’s not even a .com. The real URL for PayPal is paypal.com. (You can check an email’s validity at https://email-checker.net/ or simply search the company to see what their real URL is. )
- Don’t open attachments. These are also used to install a virus or malware. Hackers pretend to be sending you a bill or invoice, or some other item that may appear to be transactional. Always confirm that the attachment is from a legitimate source. Call the bank or credit card company and ask them. (Don’t use a phone number provided in an email.) My parents and I always double check with each other before opening attachments or links from each other, even when we’ve talked about sharing information this way.
- Look for bad English. Many hackers are not native English speakers and it shows in their word choices.
- You did not get a sudden windfall from an unknown source. Anyone claiming you have money coming to you is questionable. Don’t click on anything in these emails either.
Ways to Protect your email account:
- Change your password. Updating your password every so often can make hacking more difficult. Again, keep in mind that hackers are going after the companies too, because that’s where they can get to your information. If you change passwords, the information they have can become obsolete.
-
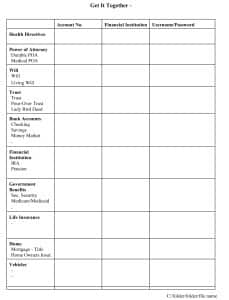
Get It Together Template DO NOT include sensitive information in your emails. If a hacker has gotten into your email, they can open anything in your emails, including attachments.
a. Don’t store passwords there.
b. If you have reset a password, delete the reset email so a hacker can’t use it.
c. It just might be time to revert to some more traditional ways of storing information. Paper and pen/pencil are probably the safest way to store your usernames and passwords. An address book is a great tool for this (or use the template provided in the Family Caregiver article at https://dinerwearadultbibs.com/the-family-caregiver/). Enter by company name. Record the company’s URL (website address), your username, and password. Then put that address book in a safe place in your home, away from anyone who might not have your best interests at heart.
- DO NOT click a link to a website and start entering personal information. This is another way hackers collect your personal information which they can use for identity theft.
Follow all these safety tips for any clicks/links you come across. And always be on guard when someone asks for personal information, whether it’s via email or phone call.